5 min read
Streamlining ERP Processes: Unlocking the Benefits of Value Stream Mapping
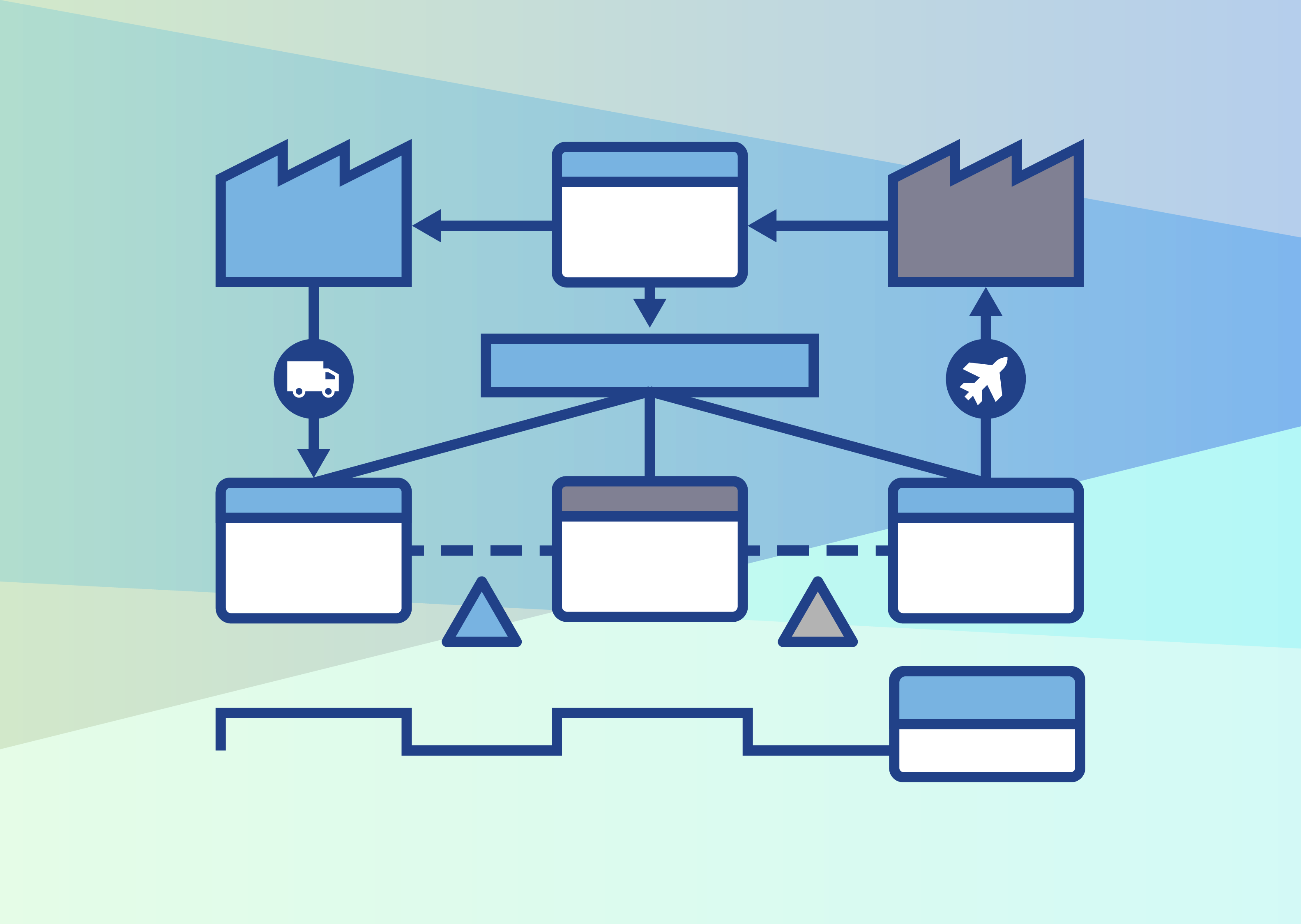
Organizations must optimize processes and improve operational efficiency for sustainable growth in today's competitive landscape. Value stream mapping (VSM) is a proven...