7 min read
The Ultimate Guide to DDoS: How To Protect Your Organization
 Joseph Ugalde
:
Nov 30, 2021 4:43:30 PM
Joseph Ugalde
:
Nov 30, 2021 4:43:30 PM

In the current era of digital supremacy and with countless businesses and organizations entirely reliant on a vast array of online services to properly function, the issue of online protection has never been more relevant. Organizations face countless threats when operating within the online world, and they must be prepared to defend against said threats at all costs. The trusted business technology professionals here at Systems X are dedicated to providing some of the best cybersecurity solutions available on the market while instructing you on how you can keep your organization safe from various online attacks.
Please continue reading to find out everything you’ll need to know about the dangers of DDoS attacks and what you need to do to protect your organization from their wide range of disastrous effects. Also, consider exploring the expertly written educational resources provided by Systems X for more information on essential online security.
Systems X provides IT solutions and strategic IT guidance with a human touch. Connect with us to talk about your options.
How Does a DDoS Attack Work?
A Distributed Denial of Service (DDoS) attack, otherwise known as a Distributed Network Attack, is a form of online assault that aims to take advantage of the specific capacity limits of various network resources, including the particular infrastructure that enables company websites to function. While these attacks aren’t usually as much of a concern to people as malware and ransomware, they can wreak significant havoc on people’s websites with little warning.
DDoS attacks work by rapidly sending multiple requests to attack a company’s web resource to exceed the website’s capacity to handle multiple requests at a single time. These attacks aim to prevent the website from functioning correctly due to its inability to manage the number of requests. Such attacks work to quickly slow sites down or even crash them by flooding them with requests. These attacks can result in many problems for businesses, including significant financial losses (especially for prolonged DDoS attacks), reputation, and brand damage. They may even lead to a loss of trust by consumers.
While many websites could theoretically be the victim of a DDoS attack, the most common targets typically include online casinos, internet shopping sites, and businesses or organizations that operate by providing online services to users.
RELATED: What Are IT Risks (+ IT Risk Management Plan Template)
Types of DDoS Attacks
One significant issue with DDoS attacks is that there are several types that cybercriminals can efficiently utilize to damage the websites of businesses. Different DDoS attacks work to target and disrupt various components or “layers'' of network connections. The OSI Model, for example, breaks up communication systems of computer networking into seven abstract layers in what’s known as a protocol stack:
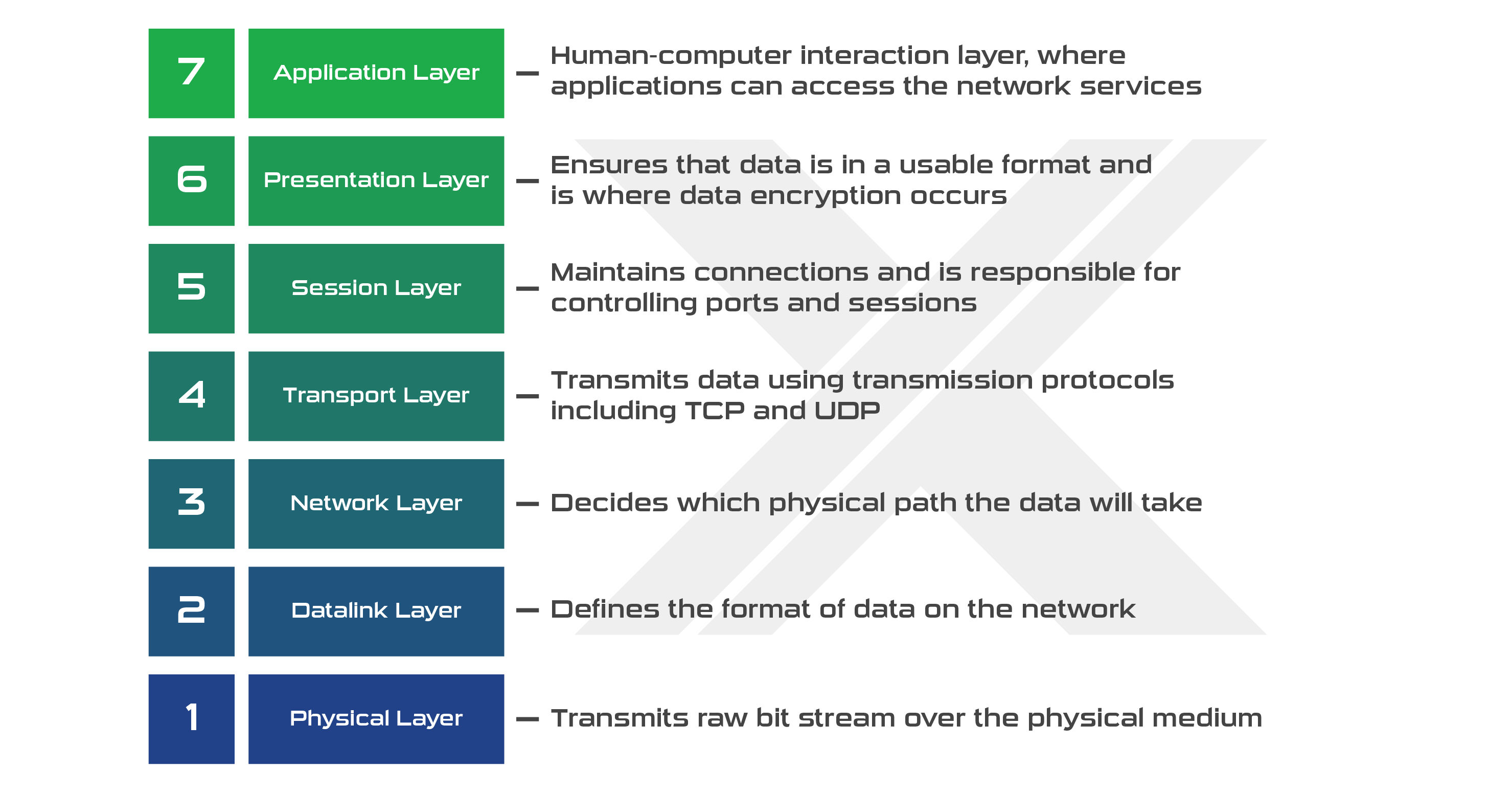
Some common types of DDoS attacks include:
Application layer attack
Often known as a Layer 7 DDoS attack, this type of attack aims to exhaust a target network’s resources to cause a denial-of-service by targeting the layer where web pages are naturally generated on servers and delivered due to HTTP requests. While a single HTTP request is computationally cheap to execute by clients, it can be expensive to respond to by target servers. Layer 7 attacks can be hard to defend against because it’s difficult to distinguish between regular, legitimate web traffic and malicious traffic.
HTTP flood
An HTTP flood is an amplification layer attack that functions similarly to pressing the refresh button on a web browser repeatedly and across many computers at once. This produces many HTTP requests that flood the server, causing slower connections, denial-of-service, and even website crashes. Simple HTTP floods can attack one URL with various attacking IP addresses, user agents, or referrers. While more complicated attacks can involve strikes from multiple IP addresses targeting random URLs with random user agents and referrers.
Volumetric attack
A volumetric attack is conducted to create a large amount of congestion in a network by actively consuming all available bandwidth between a specific target and the internet. Volume attacks occur when large amounts of data are sent to a target through amplification or another method of creating passive traffic levels, such as botnet requests.
DNS amplification
In short, DNS amplification is similar to someone calling a restaurant and saying, “I’d like to order one of everything on the menu. Please call me back and repeat the entire order.” However, the number they provide for the callback is actually the attack victim’s number. Basically, these attacks quickly generate long responses that are sent to a victim’s spoofed IP address, clogging up resources and causing system problems.
Protocol attack
Also referred to as state-exhaustion attacks, protocol attacks cause service disruptions by intentionally over-consuming server or network equipment resources, like load balancers or firewalls. This type of DDoS attack targets weaknesses specifically present in layers 3 ( the network layer) and 4 (the transport layer) of the protocol stack to make their target inaccessible to users.
SYN flood
SYN floods are a protocol attack that can be compared to a worker in a store supply room receiving requests to grab goods and then bringing them to the front once they receive confirmation. The attack, in essence, spams the worker with more package requests without sending confirmations until they can’t carry anymore and become overwhelmed. This means that requests start going unanswered.
Such attacks exploit the network connection between two computers through which communication sequences occur. The targeted machine responds to each request but is left waiting for confirmations that never come, resulting in exhausted resources.
How To Identify A DDoS Attack
DDoS attacks of different types tend to produce a single common symptom, causing their target site to become slow or unavailable to users. However, one issue with that is that such symptoms can result from many factors, not just DDoS attacks. For example, legitimate spikes in the website traffic of an online store around the holidays are normal and can cause these same performance issues. Due to this, an investigation into the matter is typically required to see if a DDoS attack occurred.
However, there are various traffic analytics tools websites can use to spot some of the more common signs of DDoS. Some of these attack signs include:
- Odd traffic patterns, such as spikes at strange hours or patterns that appear unnatural (such as recurring spikes every 15 minutes)
- Suspicious amounts of traffic generated from a specific IP range or single IP address
- A strange surge of unexpected requests to a single endpoint or page
A suspicious flood of traffic from users who appear to share a single profile of behavior, including web browser version, device type, or geolocation
However, businesses and organizations should keep in mind that there is a wide range of other, more specific DDoS attack signs that can appear, depending on the type of attack that’s occurred.
RELATED: Your Guide To DOD Compliance
Is Launching a DDoS Attack Illegal?
Potential cybercriminals should be fully aware that launching any DDoS attack against another person or business is highly illegal in the United States. In some cases, a DDoS attack can even be classified as a federal crime according to the Computer Fraud and Abuse Act (CFAA). This Act was enacted in 1986 as an amendment to the federal computer fraud law meant to address harmful hacking practices. The usage of stressors and booster services are also considered notable violations of the CFAA.
Cybercriminals found guilty of intentionally launching or conspiring to launch a DDoS attack to cause harm to a computer or server could be prosecuted and charged with a prison sentence of up to 10 years. Any individual, business, or organization believing they may have been the victim of a DDoS attack should seek out legal advice and consider investing in updated cybersecurity solutions with a trusted provider.
Are DDoS Attacks Still Happening?
Not only are DDoS attacks still happening regularly, but the occurrence of such attacks is also likely increasing. DDoS attacks increased by 20% between 2019 and 2020, and 2020 ended up being a record-setting year with more than 10 million attacks taking place. With so many attacks occurring, professionals within the cybersecurity industry have come out to state that everyone should consider themselves at risk.
A vast amount of these attacks were made to target specific industries vital to life during the chaos of the global COVID-19 pandemic. Cybercriminals were and are actively trying to exploit the vulnerabilities created by massive surges in internet usage from remote workers, who no longer had the luxury of being protected by enterprise-grade security measures at their physical offices. Other industries in healthcare, e-commerce, online learning, and streaming services have also been the frequent targets of DDoS attacks during this time.
Businesses in all industries need to understand that they are at some level of risk for being the victim of a DDoS attack. It’s essential that everyone, especially large, web-based organizations and businesses, take the time to research and invest in cybersecurity solutions to keep themselves and their livelihoods safe from the effects of DDoS attacks.
RELATED: 15 Technology Challenges Businesses May Face In 2021
How To Protect Your Organization From A DDoS Attack
Aside from using the cybersecurity services of trusted industry professionals like Systems X, what other ways can businesses protect themselves from the effects of DDoS attacks? Below are some of the four best methods to help protect yourself and your business:
Have support in close contact if an attacker strikes
It’s essential to maintain a clear communication channel with your internet service and cloud providers, as their rapid response and support will be integral in reducing the damaging effects of a DDoS attack. Most services will provide you with contact information to utilize in the event of such issues, so please contact them right away if you find yourself the victim of one of these attacks. The longer you wait to reach out, the more damage your system is likely to sustain.
Know about possible threat groups
Conduct extensive research and develop a large, continually-updated knowledge base of primary threat groups. Take note of any known tactics and preferred techniques these groups like to utilize during their attacks. Taking the initiative to prepare yourself and gather this information will help you know what to do should an attack or threat event occur and help you better monitor potential spoofs and impersonations.
Monitor your internet footprint
Ensure that you’re monitoring the internet exposure of your business and its various employees to keep general track of your digital footprint. Also, keep a record of all your critical assets and know-how to keep them secure to help prevent surprise attacks from cybercriminals utilizing DDoS methods.
Protect your IoT Devices
Always ensure that all personal and business devices that connect to the internet are highly secure to have the best chance at preventing issues from attacks. Stay on top of system updates, utilize long, complicated passwords, and actively keep unsecured IoT devices off your primary working network.
How Systems X Can Help Protect You
The trusted industry experts at Systems X are dedicated to providing their clients with the best cybersecurity solutions to keep their businesses safe from the harm of various online threats. Their team of IT veterans has extensive experience addressing complex technical problems with their vast array of top-quality services. Please consider contacting them today to learn about everything they’ll be able to do for your business’s cybersecurity. Also, don’t forget to explore their range of other essential services in the realms of IT management, consulting and advising, cloud solutions, software development, and more
Allow your team to work anywhere, any time, with total peace of mind through our customized cloud solutions.

What Are IT Risks (+ IT Risk Management Plan Template)
Every modern business faces some form of IT risk. From the smallest “mom and pop” store to the largest multinational conglomerates, there are always...

URL Phishing: What It Is And How To Prevent It
With everyone growing increasingly reliant on technology and the digital realm gaining so much power over the physical realm, the concept of ...