Why You Need an MSP That Knows NIST 800-171 Compliance
Modern businesses have to meet a lot of different regulatory compliance standards—and the specific standards they need to meet may vary depending on...
6 min read
 Mike Brattain
:
Feb 17, 2021 5:30:00 PM
Mike Brattain
:
Feb 17, 2021 5:30:00 PM
Some of the big questions different organizations have about their IT are often about the need for regulatory compliance and for strong IT security. Sometimes, there’s a bit of confusion about the difference between IT compliance and IT security because of how much the two tend to overlap.
However, it is important to understand the distinction between IT security and compliance. Why? Because, although the two are closely linked, achieving one doesn’t necessarily mean you’re meeting the needs of the other.
What is IT compliance? What is IT security? How are the two different? Where are the similarities between them? And, why does every business need to strive to meet both IT policy compliance and information security goals?
Before you crack open the Compliance for Dummies handbook, here are some things to know about IT compliance and IT security:
IT compliance is when an organization attempts to follow a set of regulatory compliance guidelines set forth for them by some other entity. In most cases, this involves governmental regulatory standards or certain industry-mandated standards that an industry organization imposes.
Examples of regulatory compliance standards include:
These are just a small handful of the different governmental and industry-mandated IT compliance standards a company might have to deal with. Other compliance requirements and standards may apply depending on the industry a business is in or even depending on specific clients or customers the company works with. For example, some organizations, like the Department of Defense, might impose extra requirements on their vendors.
RELATED: How to Perform an IT GAP Analysis
Whether your enterprise needs to comply with regulations largely depends on several factors:
Every industry has specific regulations and laws governing privacy and transparency. Some industries have specific federal acts requiring IT compliance, while other rules and standards may be optional. Some US laws like the Sarbanes-Oxley Act of 2002 (SOX) apply to almost all privately and publicly held enterprises to ensure corporate governance and financial disclosure.
Because IT compliance is driven by your industry, you’ll want to research and identify all mandatory regulations, standards, and laws that apply to your business. You may also need to comply with optional privacy standards based on customer needs and demands.
Once you’ve identified all laws, standards, and regulations, you’ll want to conduct an IT audit to assess where your business has deficiencies in maintaining compliance and ensuring security. To do an audit, you can form an internal team or utilize a third party. Depending on your industry, you may need validation from a third-party IT audit to provide transparency.
IT compliance is the actions taken by an organization to ensure standards and regulations are met. An IT audit evaluates and monitors the business’s ability to maintain these standards. There are several key differences between IT compliance vs. an IT audit.
RELATED: What's the Real Cost of Bad Security Compliance?
IT security, also known as information security or cybersecurity, is the term for the policies, procedures, and tools that a business uses to protect its data from loss or illicit use by others. Goals in an IT security plan typically focus on maintaining IT asset uptime, keeping sensitive information confidential, and ensuring that data integrity is preserved.
IT security professionals are often most concerned with assessing the specific cyber threats which will have the biggest impact on a business and employing tools, policies, and procedures to counter those threats. This often means performing a threat assessment that looks at how likely specific threats are to target the business, what the impacts of those threats are, and how they could be countered.
For example, if a business stands to lose a lot from phishing attacks and is frequently targeted by them, a cybersecurity engineer might recommend installing an anti-phishing software and training employees to recognize and avoid phishing attacks.
If ransomware is a threat, the cybersecurity specialist might recommend creating a remote backup of the business’ mission-critical data. This way, if the company’s data is corrupted by ransomware malware, then they can restore the corrupted data from the backup.
One of the goals of IT security is making the biggest impact on security for the smallest spend. So, cybersecurity pros tend to focus on making the smallest possible fixes that address the cyber threats with the biggest potential impacts and the highest chance of happening.
Several factors challenge the current IT security landscape, shaping how businesses approach their IT security policies, procedures, and processes. Here are a few driving factors that threaten most enterprises:
The COVID-19 pandemic challenged how businesses operated, and many companies were forced to move to a remote workforce. This became a logistical security nightmare for IT as they scrambled to secure personal networks and resources.
This continues to be a massive challenge for the security landscape because businesses must now protect personal computing assets and networks.
The digital divide continues to be a significant problem in the US, where segments of society have limited access, outdated technology, and insecure connections. Most of the public is also unaware of the growing threats and the needed steps to protect their technology from exposure and malware.
This affects businesses that interact with customers that may have compromised technology and connections. IT will need to educate its customers, employees, and partners about these threats and fortify its networks and systems from threats that capitalize on the digital divide.
As more and more devices, tools, and technology become smart and networked, it also opens the door to cyberattacks. And as everything becomes interconnected, disruptions from a few devices can cripple the enterprise’s infrastructure. Facebook’s recent shutdown is a prime example of internal systems crashing the entire infrastructure.
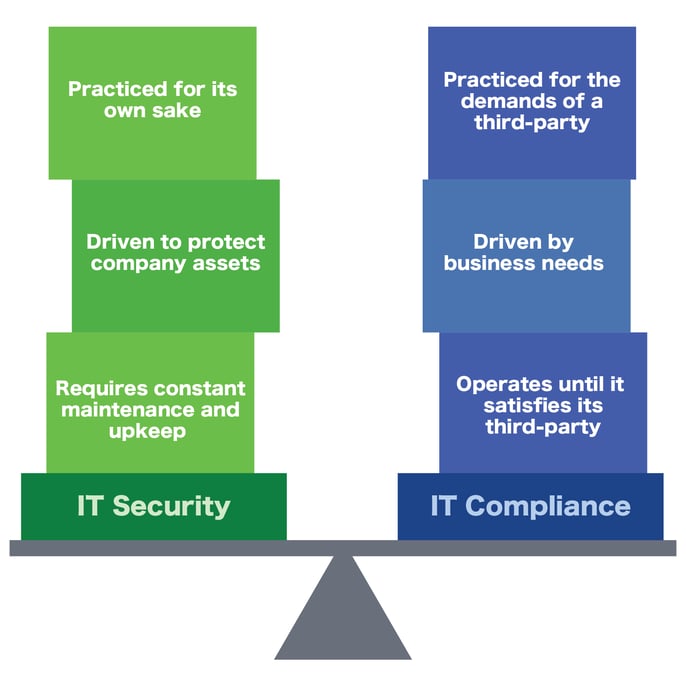
So, what makes IT compliance different from IT security? Where do the two overlap?
Some of the key differences between IT compliance and IT security are:
So, where do IT compliance and IT security overlap? Some of the key similarities include:
Saying “should I strive for IT compliance or strong IT security?” is kind of like saying “should my car have wheels or brakes?” Without both, you just aren’t going to go very far.
Companies need to strive to both meet their regulatory compliance requirements and optimize their security measures to defend against cyberattacks. Without compliance, companies open themselves up to audit risks and potential penalties that can keep them from doing business. Without strong security, companies are at risk of losing everything: Intellectual property, sensitive customer data, payroll information, accounts receivable data—everything.
So, it’s vital for companies to strive for both compliance and security in their IT infrastructure.
Need help building a strong cybersecurity framework for your business that meets both your compliance and security needs? Reach out to Systems X today! For more information on cybersecurity and other IT topics, subscribe to the blog:

Modern businesses have to meet a lot of different regulatory compliance standards—and the specific standards they need to meet may vary depending on...

Keeping your business safe isn’t usually a single step. It’s a series of vital steps designed to build a barricade around you and your most vital...